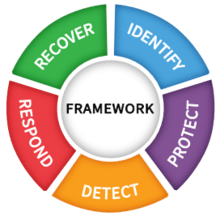
Identify
Vulnerability Management
& Analytics
File Integrity Monitoring
Regulation & Compliance Management
Mobility Management
and/or Security (MxM)
Network Vulnerbility Assessment and/or Penetration TestNew Paragraph
Protect
Security Awareness Training
Gateway/Firewall
Gateway Advanced Persistent Threat Protection
Gateway Application Control
Sandboxing or Advanced Threat Protection (ATP)
Network Intrusion Prevention System
Endpoint Protection
Endpoint Application Control
Email Protection and/or Anti-Spam
Email Encryption
Data Loss Prevention (DLP)
Multi-Factor Authentication (MFA) and/or Single
Sign-On (SSO)
Network Access Control (NAC)
Change Control
Disk Encryption
File/Folder Encryption
Virtual Private Network (VPN)
Cloud Access Security Broker (CASB)
Secure Wireless
SSL and/or DNS Protection
Software-Defined WAN (SD-WAN)
Detect
Security information and event management
(SIEM) and/or Log Management
Network Vulnerability Assessment and/or
Penetration Test
Endpoint Detection and Response (EDR)
Security Operations Center as a Service (SOCaaS)
and/or Managed Detection and Responce (MDR)
User and Entity Behavior Analytics (UEBA)
Respond
Forensic Analysis
Incident Response
Patch Management
Recover
Backup and Disaster Recovery
Data Archiving
Email Archiving
High Availability and/or Continuity
Helping organizations to better
understand and improve their management of cybersecurity risk
If you do not see the vendor that you require, just let us know and we will source them for you.
PRODUCTS BY MANUFACTURER:
- Acronis
- Alcatel-Lucent Enterprise
- Alert Logic
- Alien Vault
- Allied Telesis
- ArcServe
- Arctic Wolf
- Aruba Networks (HPE)
- Avast/AVG
- Axcient
- Axiad IDS
- Binary Defense
- Bitdefender
- Blancco
- Check Point
- Cisco
- Citrix
- Code42
- Cofense
- CriticalStart
- Dell Technologies
- Digital Hands
- Egnyte
- ERMProtect
- ESET
- F5
- FireEye
- Forcepoint
- Foresite
- Fortinet
- HP Inc.
- IBM
- Imperva
- Infoblox
- Intermedia
- IPVideo
- Ivanti
- Juniper
- Kaspersky
- Lantronix
- Lookout
- McAfee
- Meraki (Cisco)
- Microsoft
- Mimecast
- MinerEye
- NETSCOUT
- NormShield
- Nyotron
- NS1
- NS8
- Okta
- OneLogin
- Opengear
- Palo Alto Networks
- Perimeter 81
- Pixm
- Proofpoint
- Pulse Secure
- RMail
- RSA
- SonicWALL
- Sophos
- Symantec
- Tenable
- ThreatDown, powered by Malwarebytes
- TIBCO
- Trend Micro
- TrustArc
- Trustifi
- Ubiquiti
- Veeam
- Veritas
- Viavi
- VMware
- Votiro
- WatchGuard
- ZEROSPAM
- Ziften
- Zyxel
Desktop Security:
- 2FA
- Absolute Software
- Acronis
- Avast
- AVG
- Avira
- Axis Communication
- Beyond Trust
- Bitdefender
- BullGuard
- CA
- Check Point
- Comodo
- Device Lock
- Digital Defense, Inc.
- Eset
- Fortinet
- F-Prot
- F-Secure
- GData
- GFI
- Ivanti
- Kaspersky Lab
- Microsoft
- Netwrix
- Norton
- Panda
- Proof Point
- RSA
- Sophos
- Spectorsoft
- Symantec
- ThreatDown, powered by Malwarebytes
- Trellix (formerly McAfee)
- Trend Micro
- VIPRE (formerly ThreatTrack)
- Webroot
- Websense
Network Security:
- Alien Vault
- Barracuda
- Blue Coat
- Brocade
- CA
- Check Point
- Cisco
- DataMotion
- Dell
- Digital Defense, Inc.
- Exodus
- F5
- Fire Eye
- Firemon
- Fortinet
- HP
- HP Wolf Security
- Huawei
- IBM
- Imperva
- Ivanti
- Juniper Networks
- Kaspersky Lab
- Network Box 5
- Netwrix
- Palo Alto Networks
- ProofPoint
- RSA
- SafeNet
- Samsung Knox
- SonicWALL
- Symantec
- ThreatDown, powered by Malwarebytes
- Trellix (formerly McAfee)
- Trend Micro
- Tripwire
- WatchGuard
- Webroot
- Websense
- Acsi
- ACTi
- Adams Rite
- Aiphone
- Alarm Controls
- Asure ID
- Arecent Vision
- Arrow
- Awid
- Axis Communication
- Baldwin
- Bosch
- CardExchange
- CardPresso
- CameraVision
- Canon
- CloudBadging
- Cisco
- Computar
- Corbin Russwin
- Datacard Group
- Dexter Commercial
- Digimerge
- DIGIOP
- D-Link
- Don-Jo
- Dorma
- Dotworkz
- DSC
- DVTel
- EasyLobby
- EDIsecure
- EPI Suite
- EverFocus
- Evolis
- Exacq Technologies
- Falcon
- Fargo
- Flir
- Folger Adam
- Glynn-Johnson
- Hager
- HES
- HID
- Honewell
- IDP
- Interlogix
- Intransa
- ipConfigure
- Ives
- Jolly
- JVC
- KABA ACCESS
- KABA MAS
- Kaba Multihousing
- Keri Systems
- KeyScan
- Kwikset
- L-1 Identity
- LCN
- Lenovo
- MagiCard
- March Networks
- McKinney
- Medeco
- Milestone Systems
- MOBOTIX
- National Hardware
- NBS
- Netgear
- Next Level Security
- Nisca
- Norton
- OnSSI
- Open Options
- Panasonic
- Paxton Access
- Persona by Fargo
- Pegasus
- Pelco
- Rixson
- RCI
- Rhombus
- Samsung
- Sargent
- Schlage Commercial
- Schlage Electronics
- Schlage Residential
- SDC
- Securitron
- Sony
- STOPware
- Suprema
- TRENDnet
- TruCredential
- Verkada
- VIAAS formerly CudaCam
- Video IQ
- Von Duprin
- Westinghouse
- Yale Commercial
- Yale Residential
- Zebra
Access & Identity Management:
- Adallom
- Authentify
- Avatier
- Axiomatics
- BetaSystem
- BeyondTrust
- Brainwave
- CA
- Covisint
- Courion
- Cryptzone
- Cyberark
- Deepnet Security
- Dell Software
- DeviceLock
- Duo
- EMC
- Entrust Datacard
- Exostar
- Fischer
- Gigya
- GlobalSign
- Great Bay
- Hitachi ID
- IBM
- Identity Automation
- Identropy
- Ilantus
- Imanami
- LastPass
- Lieberman Software
- Microsoft
- NetIQ
- Observe IT
- Okta
- One Login
- Oracle
- Prolifics
- Quantum Secure
- RES Software
- SafeNet
- SailPoint
- Savynt
- SecureAuth
- Simeio
- SpectorSoft
- STEALTHbits Technologies
- Tuebora
- Thycotic
- UnboundID
- Usher
- Wave
- WWPass
- Xceedium
Mobile Device Management (MDM):
- Absolute Software
- Airwatch
- Blackberry
- Citrix
- IBM
- Ivanti
- Kaspersky Lab
- MaaS360
- Mobile Iron
- N-able
- Scalefusion
- Sophos
- Soti
- Symantec
Distributed Denial-of-Service (DDoS):
- A10 Networks
- Akamai
- Arbor Networks
- Check Point
- CloudFlare
- Corero Network Security
- DOSarrest
- F5 Networks
- Huawei
- Imperva Incapsula
- Juniper Networks
- Neustar
- NimbusDDoS
- NSFocus
- PacketViper
- Radware
- Zenedge










